Fortify overview
Small businesses are increasingly reliant on Microsoft cloud applications, but these applications can also be a target for malicious actors. MSPs play a critical role in helping small businesses protect their Microsoft tenants, but they often face challenges in managing security across multiple customers and applications.
Fortify is a simple and effective way for MSPs to secure Microsoft tenants. The platform provides the tools MSPs need to improve the security of their customers' Microsoft tenants, save time and effort, and improve communication with their customers.
Problem
Managing security across multiple customers and applications can be a daunting task. MSPs need to understand the constantly evolving threats and vulnerabilities, as well as the mitigation strategies. They also need to effectively communicate cybersecurity with their customers.
Solution
Fortify is a simple and effective way for MSPs to secure Microsoft tenants. The platform provides an easy-to-use interface along with Recommended Actions for Microsoft to allow MSPs to select their connected organizations and deploy recommended best practice security protocols in minutes.
Features
- Recommended Actions: Fortify provides Microsoft Recommended Actions for each connected organization and product. MSP admins need only select the organization and request to enable the recommended security settings.
- Fortify also provides Recommended Actions based on other frameworks such as CISA (for example, Enhanced Monitoring to Detect APT Activity Targeting Outlook Online).
- One or more Recommended Actions can be deployed to one or more organizations simultaneously.
- Recommended Actions can be undone.
- Reporting: Fortify generates two powerful reports. The first report, Organization Vulnerability Assessment, can be used to communicate the Microsoft tenant’s current security posture and sell new services.
- Reporting: the second report, Threat Mitigation. can be used to communicate the Microsoft tenant’s security posture after applying Fortify Recommended Actions, ongoing threats, and proactive Respond policies.
- New Recommended Actions will be added over time.
Benefits
- Increased security: Fortify helps MSPs to improve the security of their customers' Microsoft tenants by deploying recommended best practice security protocols.
- Reduced time and effort: Fortify saves MSPs time and effort by automating the process of securing Microsoft tenants.
- Improved communication: Fortify provides MSPs with the tools they need to communicate effectively with their customers about security.
- Increased sales: Fortify can help MSPs to sell new security services to their customers.
Requirements
- SaaS Alerts MSP Admin privileges.
- Accept all Fortify module security permissions.
- A global admin account that is specific to the organization domain to connect to Fortify.
Implementation best practice
When getting started with Fortify, we recommend testing on your own tenant before applying policies for your customers.
Enabling Fortify
Click the Fortify icon, read and agree to the check box items, and click Turn on Fortify.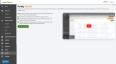
Connecting the Microsoft tenant
Click Microsoft + and connect desired tenants to Fortify.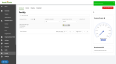
Be sure to OAuth with the right Microsoft tenant with a global admin and Consent on behalf of your organization.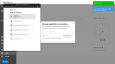
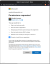
NOTE We specifically require another OAuth connection in order to adhere to the least required privilege principle best practice.
Enabling recommended actions
After connecting Fortify to a Microsoft tenant, you will see its Secure Score in the Dashboard tab.
Click Fortify to review this tenant’s recommended actions.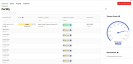
By default, the Actions page shows you available actions for the tenant.
NOTE Some actions are simply not possible to automate via API, others still need to be evaluated for integration potential and some are restricted by license.
Click the magic wand or use the check box to select multiple actions you wish to apply. If using the check boxes, click Next.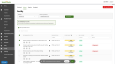
Review the pending actions and click Apply Actions. 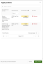
This will initiate your desired action(s) with Microsoft, and you will see a green success toaster or a red error toaster if any issues come up.
Ongoing recommended actions
At this time, most of the Fortify recommended actions come from Microsoft and will remain in an Ongoing status until their points are incorporated into the tenant’s score. This is due to the once every twenty hour frequency employed by Microsoft to recalculate the score.
It’s important to understand that if the success toaster indicates the action is done, it’s done. Its effect on the score however, could take up to twenty four hours to appear.
Disabling recommended actions
Head over to the Completed tab where you can select one or more recommended actions to undo.
Tag definitions
| Tag Name | Tag Definition |
| Alternative mitigation | MSP has indicated that they are accomplishing this policy with another mechanism and will not apply the recAction via Fortify |
| Apply failed | When Fortify attempted to apply the policy, Microsoft returned an error captured in the History and the policy was not applied successfully |
| In progress | recAction has been selected to be applied, but Microsoft has not yet flagged it as having been completed yet |
| MS licensed | recAction is available for the tenant, however, Microsoft is not listing it as available from within the tenant |
| Pre-existing | Policy with the exact same name as our recAction was in place at the time that Fortify was connected to their tenant |
| Regressed | recAction was successfully applied, but a change in the tenant has made the policy not 100% applied any longer. Example, MFA applied to all accounts on Monday. A new user is onboarded on Tuesday without MFA enabled. Wednesday after syncing the tenant and Fortify the policy is marked as regressed. |
| Risk accepted | MSP has indicated that they are not going to apply the recAction via Fortify and have acknowledged the security risk associated with not applying it. You won't be given any points for this status. You can view this action in history or undo it at any time. |
| Third party mitigation | MSP has indicated the recommended action has already been addressed by a third-party application or software, or an internal tool and will not apply the recAction via Fortify. You'll gain the points that the action is worth, so your score better reflects your overall security posture. If a third party or internal tool no longer covers the control, you can choose another status. Keep in mind, Microsoft will have no visibility into the completeness of implementation if the recommended action is marked as either of these statuses. |
| Undo failed | recAction was successfully applied, MSP has then determined they did not want to apply the recAction and selected to undo this. When Fortify attempted to undo the policy, Microsoft returned an error captured in the History and the policy is still applied. |
Tag color codes
| Tag Color | Tag Definition |
| Blue | recAction in progress of being applied |
| Green | recAction successfully applied |
| Orange | recAction indicated to not be addressed via Fortify |
| Red | recAction had an issue being applied and/or hasn’t been applied |
| Yellow | recAction requires manual intervention or additional licensing |
Parameter types
Parameters are available on some recActions, we will continually release parameters to recActions. Parameters allow for configuration of policy specific to the organization/tenant. A parameter can only be applied once with one condition per recAction.Common example, Ensure MFA is Applied to all Accounts, but you want to exclude the breakglass accounts. Parameters can be used to call out these specific accounts by User. In this case the Operator of Does not include would be used and each individual email for the breakglass account(s) would be added.
The following list of parameter types is currently supported, however as we continually release parameters we will be adding to the list of parameter types.
| Parameter Type | Parameter Type Definition |
| Admin email address | Administrator email addresses can be included |
| Allow only specific domains | The specific domains that are to be included can be specified |
| Delete devices that haven’t checked in for this many days | The number of days preferred can be entered and will overwrite any previous version of the policy |
| Directory Roles | Roles that are defined in Microsoft for the tenant will be available for selection. Depending upon the Operator you can include or exclude the group(s) from the policy. |
| Groups | Groups that are defined in Microsoft for the tenant will be available for selection. Depending upon the Operator you can include or exclude the group(s) from the policy. |
| Idle session timeout | The number of minutes preferred can be entered and will overwrite any previous version of the policy |
| Large audience threshold | The number of audience members preferred can be entered and will overwrite any previous version of the policy |
| Maximum age of audit log entries (days) | The number of days preferred can be entered and will overwrite any previous version of the policy |
| Notify emails | Email address(es) can be included so that an email notification is sent to those parties |
| Quarantine policy | The number of days preferred can be entered and will overwrite any previous version of the policy |
| Send copies emails | Email address(es) can be included so that an email is sent to those parties |
| Users | User emails that are defined in Microsoft for the tenant will be available for selection. Depending upon the Operator you can include or exclude the group(s) from the policy. |
FAQ
When Fortify is added to a tenant, terms of service stipulate that upon subsequent removal of the customer organization from Fortify or from SaaS Alerts as a whole, Fortify will revert any changes made to the tenant policy configurations back to their original state.
Why hasn't the Microsoft Secure Score increased since running Fortify Actions?
The score does not impact immediately and we do not move it out of pending until the score impact is reported as improved as a result of the policy recommendation being applied. This is by design. We considered simply moving it once the change was sent to Microsoft. However, this would create a false impression of the actual completeness state of the policy change.
Microsoft recalculates the score only once in 24 hours, in addition some policies can take many days even weeks to be fully implemented.
EXAMPLE Partner implements a policy that requires all users to have MFA active and configured. Until all users actually complete their MFA setup the action will not report back to Fortify as completed, and it will sit in Ongoing. We specifically chose the term ongoing rather than pending because there is ongoing activity which must occur in the organization to get the points credit for the secure score.
We are making UI changes to make the partners more aware of the dependencies in the background.
How often is the license status of organizations connected to Fortify updated?
Every 24 hours, the cadence that Microsoft refreshes their security data / enabled security license for a tenant.
How does Fortify interact with applications such as DUO?
SaaS Alerts Fortify is reading data directly from Microsoft for each tenant to present the secure score information and recommendations.
Microsoft does not recognize third-party multifactor authentication as a legitimate solution. Recently, Microsoft has been canceling CSP accounts, and one of the reasons cited is that the partner does not have all tenants configured with multifactor authentication via Microsoft, which is a policy requirement to remain a CSP partner.
How do you track a regression?
A regression (a reduction in security score points) may be tracked using Analyze by looking for fortify action regressed using SaaS Alerts Fortify as the product selection.
Why do some organizations have a lower potential score than others?
An organizations level of Microsoft licensing will impact its potential score.


